Security engineering is a fast-moving field with an outsize impact across all aspects of business—estimates indicate that there are trillions of dollars at stake. In this ask-me-anything-style Q&A, Toptal security engineer Gökay Pekşen answers questions from software developers around the world, covering major compliance frameworks, top cloud and AWS security checks, and the importance of DevSecOps in the cloud.
Early in his career, Gökay became one of Turkey’s first Certified Ethical Hackers; he later built Turkey’s first DevSecOps continuous integration and continuous delivery (CI/CD) pipeline. He is the founder and CEO of Prime Threat, a cybersecurity consultancy that helps businesses navigate GDPR compliance and risk management, and brings 15 years of experience in IT security to this conversation.
Editor’s note: Some questions and answers have been edited for clarity and brevity.
Getting Started With DevOps and Security Engineering
What does a security engineer do? What kinds of tasks do you work on day to day?
—M.D., Seattle, United States
A security engineer safeguards an organization’s digital assets and data from cyberthreats. They assess risks, design and implement security measures, and enforce policies and procedures to ensure the integrity and confidentiality of IT resources. Security engineers conduct regular audits, manage vulnerabilities, and respond to security incidents, working to prevent breaches and mitigate their impact.
My day-to-day work varies greatly depending on what kind of project I’m working on. If it’s an information security project, I usually analyze the strategy, check the processes, adjust them to the dynamics of the respective company, and write documentation. If it’s a cybersecurity project, I usually conduct penetration tests, control the rules and configurations, and implement or improve safeguards. I like working with companies as a Virtual Chief Information Security Officer (vCISO) because I enjoy creating strategies and guiding teams on how to implement them.
Can you tell us more about how to become a security engineer? What was your path into this career?
—S.S., Minneapolis, United States
While working on my bachelor’s degree in computer engineering, I became one of the first Certified Ethical Hackers in Turkey. This naturally drove me to become a security professional. Throughout my career, I’ve always stayed focused on the fundamentals, particularly Linux, networking, and C. I’ve also invested time in training and mentoring others, which has developed my professional network and further advanced my own skills over time.
To become a security engineer, you may want to pursue higher education in computer science, information technology, or cybersecurity. Consider seeking out internships in one of these fields as well. It will take time to develop foundational technical expertise with programming languages, operating systems, and networking concepts. Familiarize yourself with cybersecurity and DevOps fundamentals, including encryption, access control, and security protocols. Beyond technical skills, effective communication and problem-solving skills are crucial for success in this field.
What path do you suggest for someone in DevOps and cloud infrastructure to extend their domain knowledge into cybersecurity and DevSecOps? Are there books or courses you would recommend?
—W.Y., Vancouver, Canada
If you are a beginner, you may start by pursuing a CEH or OSCP course—but you need more than just certifications to hone your expertise. Books like Cybersecurity Essentials by Charles J. Brooks et al. can provide a comprehensive introduction to cybersecurity fundamentals. Those with a DevOps and cloud infrastructure background should focus on cloud security and may benefit from reading Cloud Security and Privacy by Tim Mather, Subra Kumaraswamy, and Shahid Latif. From there, you can further explore DevOps security integrations by reading DevOpsSec by Jim Bird and Securing DevOps by Julien Vehent; both books provide insight into this area.
What is DevSecOps exactly, and how can organizations just getting started with it smoothly incorporate security into DevOps? For those starting from scratch, what is the optimal way to set up a security-focused culture?
—K.S., Montreal, Canada
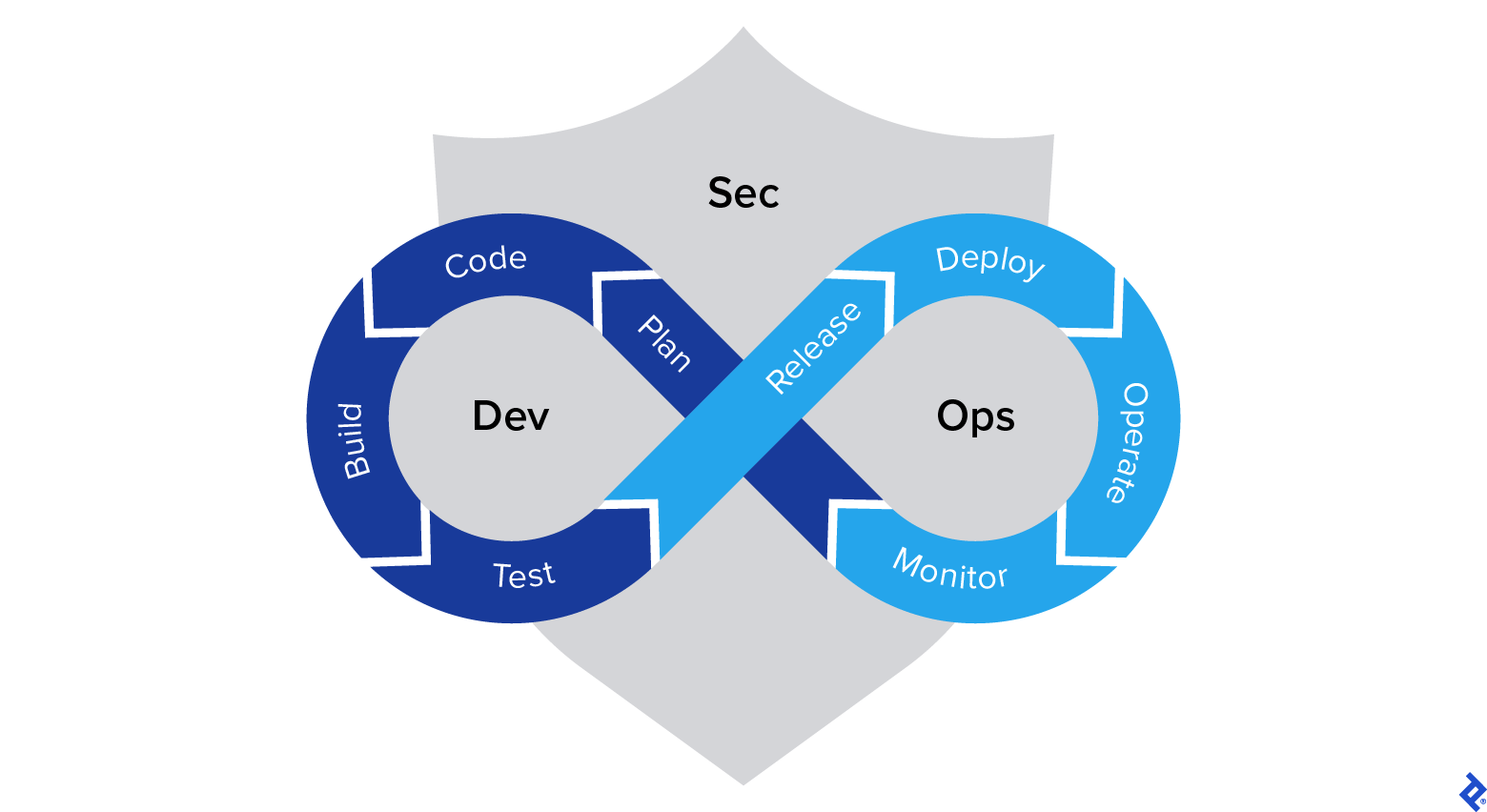
In my opinion, DevSecOps represents the most critical transformation that a business can invest in right now. Automation is a caretaker: It eliminates the risk of error, and acts independently of the negative aspects of human nature. Routines can be a burden, and manual operations invite too many opportunities for mistakes or carelessness. Repeating the same tasks can make us inefficient and cause us to lose focus and interest. As human beings we need challenges and new experiences. Who wants to deploy identical machines from a template, run the same rules over and over, or read source code until the end of time? I don’t think anyone does.
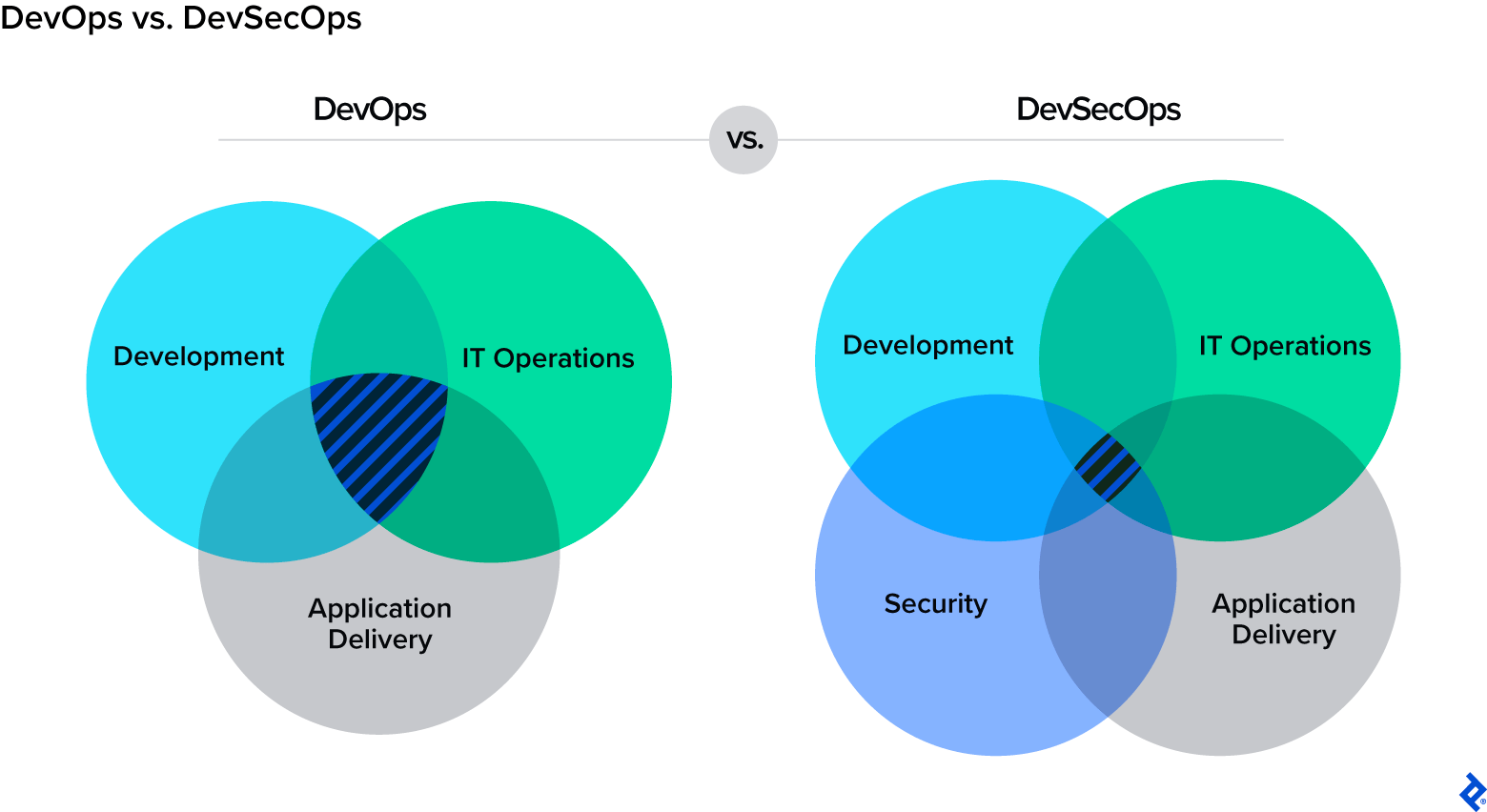
DevSecOps mixes three crucial elements of IT into one pot: development, security, and IT operations. It’s challenging to gather these giant topics together, and it’s even harder to manage them as one cohesive unit. I have implemented or otherwise been involved in many different CI/CD pipelines, and I’ve observed firsthand how operations instantly become more efficient when you eliminate the burden of manual operations.
Establishing a security culture is hard; in fact, I would say it’s nearly impossible to cultivate from the inside. There will be resistance from employees who may be set in their ways, and you will need someone to guide you and illuminate the path. Most of the time this means you will require a consultancy to step in.
Security Considerations and Best Practices for Businesses
What are the main differences between major compliance frameworks? Are any particularly suited to specific industries?
—K.S., Montreal, Canada
Frameworks and standards are identical when applied to entities or assets, but they differ for industries. Think of it this way: A firewall is a firewall—no matter where you place it. If you evaluate entities by their attributes, they will act the same in every framework. But the purpose of the entities or assets will differ from industry to industry. For example, a web server may handle financial data for a banking company, but it will handle personal identifiable information (PII) for a health institution: same entity, different sector, different outcomes.
ISO 27001 is the most common standard for security. Most of the standards and frameworks are built on ISO 27001, so that’s the best place to start, regardless of the industry. Applying it to your daily job is the easiest way to comprehend it.
What basic security checks would you recommend to test a web application?
—K.G., Łódź, Poland
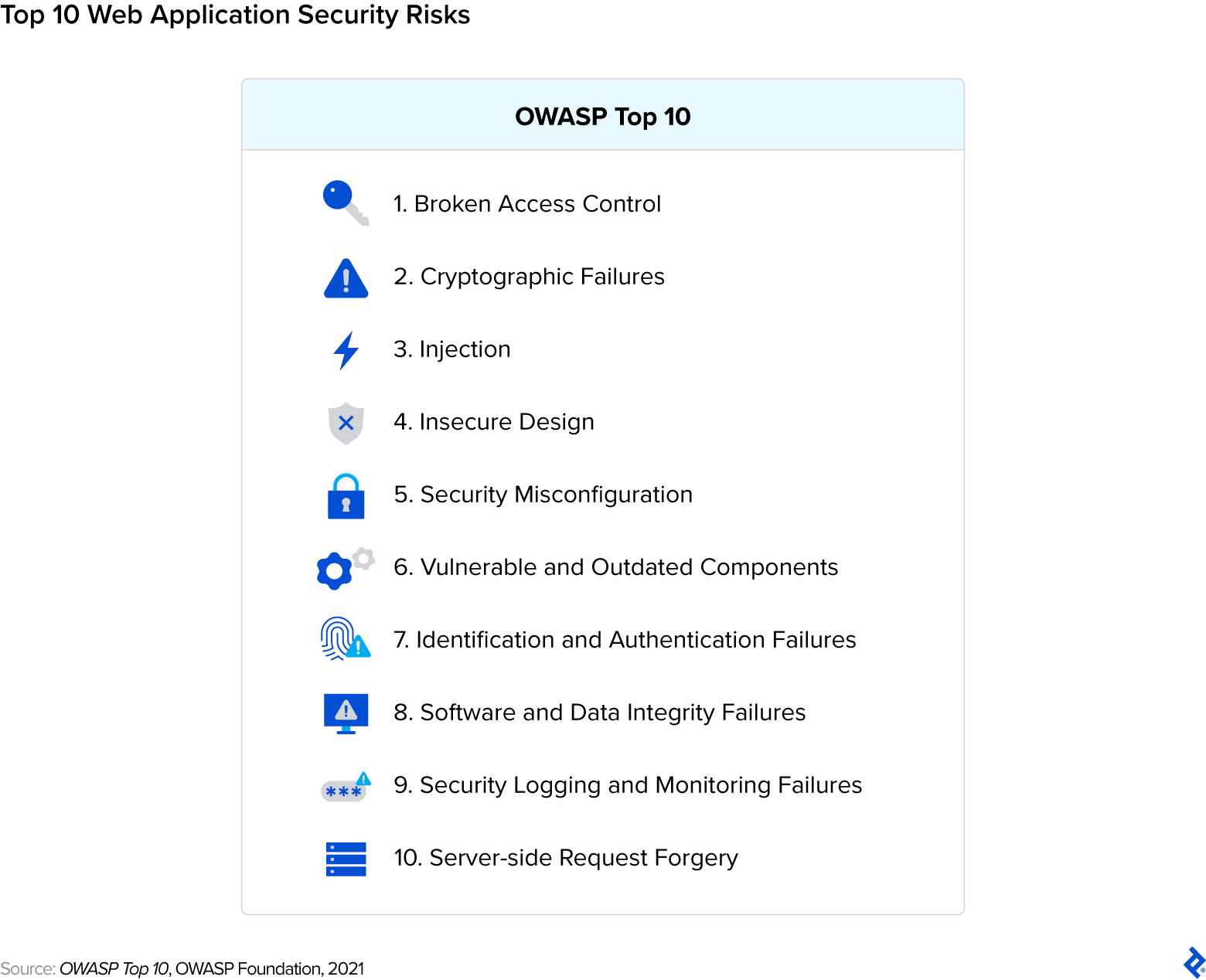
The top 10 list from Open Web Application Security Project (OWASP) is a must for web application security; I recommend it to everyone. It’s a collection of standardized and developer-friendly resources to help organizations identify, prioritize, and mitigate the most critical security vulnerabilities in web applications. It’s also updated on a regular basis.
With so many different AWS offerings, where should teams get started with regard to AWS security best practices? What are the most critical services to secure?
—K.S., Montreal, Canada
The answer to this question largely depends on what services you’re using. AWS is a vast world; there are so many different tools and services at every level of the tech stack. Identify and access management (IAM), web application firewall (WAF), virtual private cloud (VPC), CloudTrail, S3 bucket security, and infrastructure as code (IaC) tools are all great places to start, and applicable to most AWS users operating at scale. There are additional tools available for data security and automation that you may want to look into, depending on your specific use case. I’d recommend consulting with an AWS specialist to determine your needs.
The Future of Cybersecurity
Could you outline the impact of the advances in generative AI on your work?
—J.B., Vienna, Austria
I create the way, and generative AI walks the path. I tell it to create unique documentation sets to comply with specific frameworks for the companies. I ask it to check code to see if it is vulnerable to any exploits or to determine whether a configuration file may lead to a cybersecurity attack.
Generative AI feels like a whole new frontier in this field. I use it daily. It’s especially helpful when I need to quickly learn how to use new tools and technologies.
What are the challenges when implementing zero trust architecture (ZTA) in cloud-based environments?
—O.T., Istanbul, Turkey
Zero trust puts the principle of “never trust, always verify” into action, as a response to the more traditional approach of “implicit trust,” in which users and their devices are assumed to be trustworthy after they’re verified and connected to a permissioned network. ZTA is about privilege management: It aims to prevent malicious actors from moving laterally through the network to reach sensitive materials to which they weren’t explicitly granted access.
However, ZTA is a commonly misunderstood topic because security vendors are increasingly remarketing their products to capitalize on the novelty of this term, even when it might not be relevant or applicable. They often describe any firewall, endpoint protection platform, or access management tool (like IAM) as acting like ZTA—but this is not technically true. Merely applying a security product to a network is a much different experience than maintaining a culture of security within that network; no individual product can replace the ongoing work required to put ZTA into practice.
Before you implement ZTA, you must take all relevant stakeholder, shareholder, supplier, and connection relationships into serious consideration. The cloud is meant to be a more flexible and free environment than what we work with in enterprise software. To make that a reality, companies need to be meticulous about identifying what’s truly necessary to safeguard. Protecting confidential information is not just an ethical obligation—it’s also good for business. By securing your economic engine, you build trust and maintain a competitive edge.
How do you think exploits will continue to evolve? Initially we had binary injections, web exploitation, SQL injection, and HTTP compromise—not to mention good old-fashioned social engineering, like phishing. What’s next? What’s the newest trend?
—J.O., Fortaleza, Brazil
Generative AI is just now beginning to show us unique exploits and payloads that have never been seen before. It works against us. Before long, we will start to see different attack methods and exploits because of the new vectors created by AI. I wish I could say more about this, but it would be dangerous to share too many details.
Going forward, every new attack will evolve and change itself by gathering and responding to information in its environment. We’re also beginning to see attacks on AI-based operations, like data poisoning in the generative AI ecosystem. Things will change. Security professionals are already devising prompt firewalls to prevent ChatGPT data leakage.
The next big thing will be quantum security, but it may be too soon to discuss it. Quantum security is an interdisciplinary field that combines aspects of quantum physics, mathematics, and computer science, and opens up opportunities for collaboration across these domains. Forward-thinking organizations, especially those with long-term data protection needs, are exploring and adopting quantum-resistant encryption solutions to future-proof their data security.
However, it’s essential to note that while quantum security is gaining momentum, it may only partially replace traditional encryption in some use cases. Some cryptographic algorithms are computationally secure even against quantum attacks, and not all data requires quantum-resistant encryption.