There are two main ways to recover encrypted data in a ransomware attack: restoring from backups and paying the ransom. Compromising an organization’s backups enables adversaries to restrict their victim’s ability to recover encrypted data and dial-up the pressure to pay the ransom.
This analysis explores the impact of backup compromise on the business and operational outcomes of a ransomware attack. It also shines light on the frequency of successful backup compromise across a range of industries.
The findings are based on a vendor-agnostic survey commissioned by Sophos of 2,974 IT/cybersecurity professionals whose organizations had been hit by ransomware in the last year. Conducted by independent research agency Vanson Bourne in early 2024, the study reflects respondents’ experiences over the previous 12 months.
Executive summary
The analysis makes clear that financial and operational implications of having backups compromised in a ransomware attack are immense. When attackers succeed in compromising backups, an organization is almost twice as likely to pay the ransom and incurs an overall recovery bill that is eight times higher than for those whose backups are not impacted.
Detecting and stopping malicious actors before your backups are compromised enables you to reduce considerably the impact of a ransomware attack on your organization. Investing in preventing backup compromise both elevates your ransomware resilience while also lowering the overall Total Cost of Ownership (TCO) of cybersecurity.
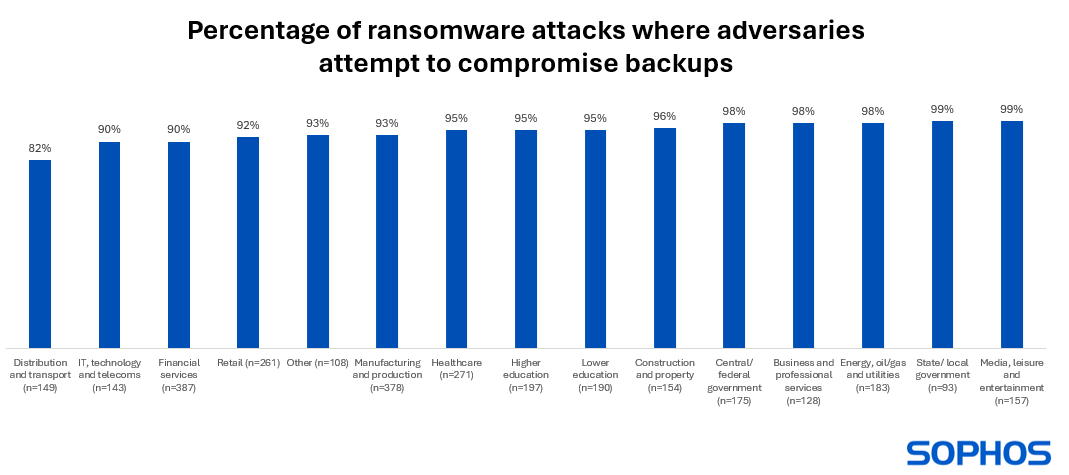
Learning 1: Ransomware actors almost always attempt to compromise your backups
94% of organizations hit by ransomware in the past year said that the cybercriminals attempted to compromise their backups during the attack. This rose to 99% in both state and local government, and the media, leisure and entertainment sector. The lowest rate of attempted compromise was reported by distribution and transport, however even here more than eight in ten (82%) organizations hit by ransomware said the attackers tried to access their backups.
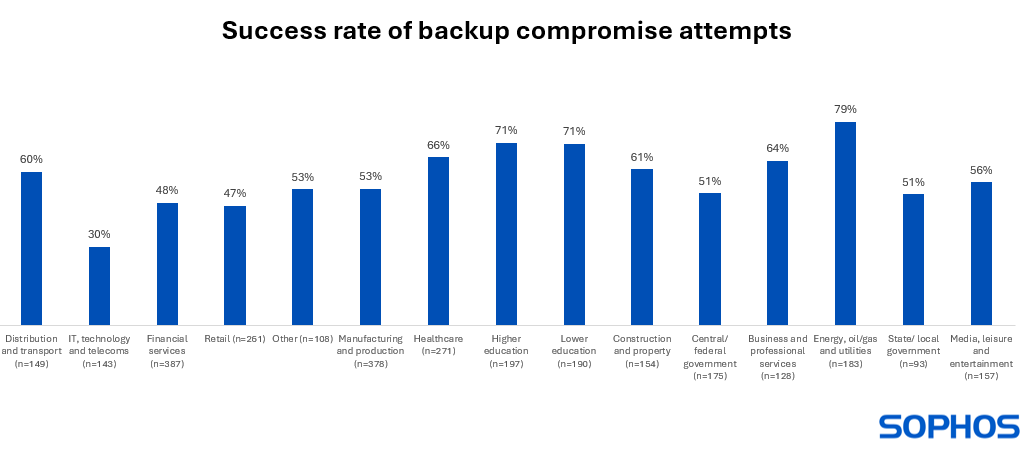
Learning 2: Backup compromise success rate varies greatly by industry
Across all sectors, 57% of backup compromise attempts were successful, meaning that adversaries were able to impact the ransomware recovery operations of over half of their victims. Interestingly, the analysis revealed considerable variation in adversary success rate by sector:
- Attackers were most likely to successfully compromise their victims’ backups in the energy, oil/gas, and utilities (79% success rate) and education (71% success rate) sectors
- Conversely, IT, technology and telecoms (30% success rate) and retail (47% success rate) reported the lowest rates of successful backup compromise
There are several possible reasons behind the differing success rates. It may be that IT, telecoms and technology had stronger backup protection in place to start with so was better able to resist the attack. They may also be more effective at detecting and stopping attempted compromise before the attackers could succeed. Conversely, the energy, oil/gas and utilities sector may have experienced a higher percentage of very advanced attacks. Whatever the cause, the impact can be considerable.
Learning 3: Ransom demands and payments double when backups are compromised
Data encryption
Organizations whose backups were compromised were 63% more likely to have data encrypted than those that didn’t: 85% of organizations with compromised backups said that the attackers were able to encrypt their data compared with 52% of those whose backups were not impacted. The higher encryption rate may be indicative of weaker overall cyber resilience which leaves organizations less able to defend against all stages of the ransomware attack.
Ransom demand
Victims whose backups were compromised received ransom demands that were, on average, more than double that of those whose backups weren’t impacted, with the median ransom demands coming in at $2.3M (backups compromised) and $1M (backups not compromised) respectively. It is likely that adversaries feel that they are in a stronger position if they compromise backups and so are able to demand a higher payment.
Ransom payment rate
Organizations whose backups were compromised were almost twice as likely to pay the ransom to recover encrypted data than those whose backups were not impacted (67% vs. 36%).
Ransom payment amount
The median ransom payment by organizations whose backups were compromised was $2M, almost double that of those whose backups remained intact ($1.062M). They were also less able to negotiate down the ransom payment, with those whose backups were compromised paying, on average, 98% of the sum demanded. Those whose backups weren’t compromised were able to reduce the payment to 82% of the demand.
Learning 4: Ransomware recovery costs are 8X higher when backups are compromised
Not all ransomware attacks result in a ransom being paid. Even when they do, ransom payments are just part of the overall recovery costs when dealing with a ransomware attack. Ransomware-led outages frequently have a considerable impact on day-to-day business transactions while the task of restoring IT systems is often complex and expensive.
The median overall ransomware recovery costs for organizations whose backups were compromised ($3M) came in eight times higher than that of organizations whose backups were not impacted ($375K). There are likely multiple reasons behind this difference, not least the additional work that is typically needed to restore from decrypted data rather than well-prepared backups. It may also be that weaker backup protection is indicative of less robust defenses and greater resulting rebuilding work needed.
Those whose backups were compromised also experienced considerably longer recovery time with just 26% fully recovered within a week compared with 46% of those whose backups were not impacted.
Recommendations
Backups are a key part of a holistic cyber risk reduction strategy. If your backups are accessible online, you should assume that adversaries will find them. Organizations would be wise to:
- Take regular backups and store in multiple locations. Be sure to add MFA (multi-factor authentication) to your cloud backup accounts to help prevent attackers from gaining access.
- Practice recovering from backups. The more fluent you are in the restoration process, the quicker and easier it will be to recover from an attack.
- Secure your backups. Monitor for and respond to suspicious activity around your backups as it may be an indicator that adversaries are attempting to compromise them.
How Sophos can help
Sophos MDR: Over 500 experts monitoring and defending your organization
Sophos MDR is a 24/7 expert-led managed detection and response service that specializes in stopping advanced attacks that technology alone cannot prevent. It extends your IT/security team with over 500 specialists who monitor your environment, detecting, investigating, and responding to suspicious activities and alerts.
Sophos MDR analysts leverage telemetry from the security tools you already use – including your backup and recovery solution – to detect and neutralize attacks before damage is done. With an average threat response time of just 38 minutes, Sophos MDR works faster than your next threat.
Sophos XDR: Enabling IT teams to detect and respond to attacks
In-house teams can use Sophos XDR to get the visibility, insights, and tools they need to detect, investigate, and respond to multi-stage threats, across all key attack vectors, in the shortest time. With Sophos XDR you can leverage telemetry from your backup and recovery solution, as well as your wider security stack, to quickly see and respond to attacks.